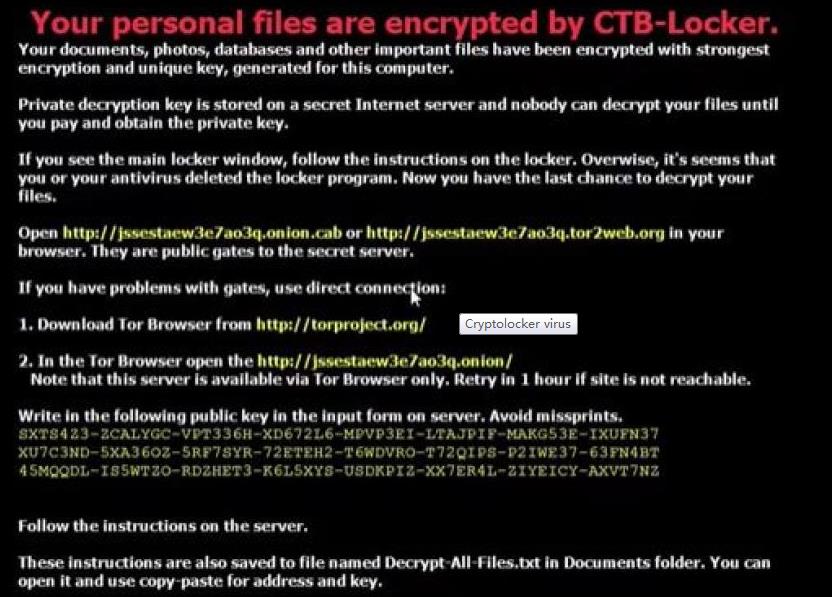
Australians are paying thousands of dollars to overseas hackers to rid their computers of an unbreakable virus known as Cryptolocker.
There has been a rise in the number of people falling victim to the latest version of an encryption virus which hijacks computer files and demands a ransom to restore them.
The “ransomware” infects computers through programs and credible-looking emails, taking computer files and photographs hostage.
Cryptolocker comes in a number of versions, the latest capitalising on the release of Windows 10.
It can arrive in an email disguised as an installer of the new operating system in a zip file.
IT technician Josh Lindsay said he had been repairing computers for 15 years but the current form of the virus was “unbreakable”.
“It’s definitely the worst I have come across,” he said.
The hackers offer computer owners a chance to retrieve data – but only if they pay a ransom using the electronic currency Bitcoin.
“If it’s on Bitcoin they can use it to purchase anything online from gold bullion, to shares, to property even and it’s virtually untraceable,” Mr Lindsay said.
Virus victim Renata Eugstar said she decided not to pay the ransom price.
“I just wouldn’t pay it out of principle, I suppose there are people out there that have to, you know, if it is a business,” she said.
Michael Bailey from the Tasmanian Chamber of Commerce and Industry said when his organisation was hit, a ransom equivalent to $US350 was paid to overseas hackers.
“It was cheaper for us to just pay rather than worry about trying to fix it,” he said.
“The advice from our IT people is – some of the best in Australia – was that it would take weeks for them to work out how to unencrypt the files, if they could at all.”
The deputy chairwoman of the Australian Competition and Consumer Commission, Delia Rickard, said over the past two months there had been a spike in the number of people falling victim to the scam.
The commission has received 2,500 complaints this year and estimates about $400,000 has been paid to the hackers.
“That’s the tip of the iceberg,” she said.
Thomas King, the general manager of the Australian Cyber Emergency Response Team (AusCERT) and part of the University of Queensland, said the number of computers infected by the virus was on the rise.
“Individuals, companies, not-for-profits, organisations of all kinds have paid and it’s a sad state of affairs that so many people do feel the need to pay because they don’t have good enough cyber security protections,” he said.
Mr King has urged people to take precautions when opening emails and to ensure good backups of any data is kept offline.