When it comes to vulnerabilities and security, Google’s Android has never been in the good books of security experts or even its users to a great extent. Now, another vulnerability has surfaced that claims to leave millions of devices affected. Security expert Gal Beniamini has now revealed another flaw in Android encryption.
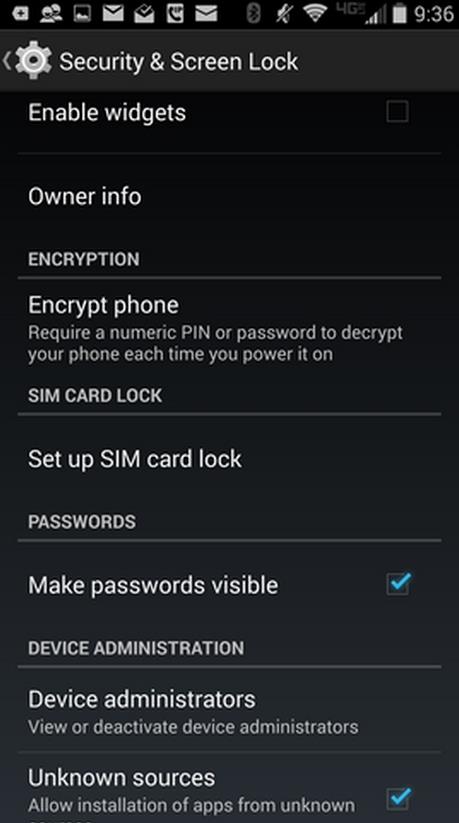
According to the DailyMail, the security researcher has said that Android devices with full disk encryption and powered by Qualcomm processors are at risk of brute force attacks wherein hackers can use persistent trial and error approach. Full disk encryption is on all devices running Android 5.0 onwards. It generates a 128-bit master key for a user’s password. The report adds that the key is stored in the device and can be cracked by malicious minds.
“Android FDE is only as strong as the TrustZone kernel or KeyMaster. Finding a TrustZone kernel vulnerability or a vulnerability in the KeyMaster trustlet, directly leads to the disclosure of the KeyMaster keys, thus enabling off-device attacks on Android FDE,” Beniamini explains.
A combination of things like Qualcomm processors verifying security and Android kernels are causing the vulnerability. Google along with Qualcomm is working at releasing security patches, but Beniamini said hat fixing the issue may require hardware upgrade.
“Full disk encryption is used world-wide, and can sometimes be instrumental to ensuring the privacy of people’s most intimate pieces of information. As such, I believe the encryption scheme should be designed to be as “bullet-proof” as possible, against all types of adversaries. As we’ve seen, the current encryption scheme is far from bullet-proof, and can be hacked by an adversary or even broken by the OEMs themselves (if they are coerced to comply with law enforcement),” he adds.
Lately, encryption debate had taken centre stage when Apple refused to unlock an iPhone belonging to a terrorist involved in San Bernardino shooting. The FBI reportedly managed to break into the device without Apple’s help and is believed to have paid a whopping $13 million to do so.