The legal saga between Apple and the FBI has thrust encryption into the government’s policy spotlight again – but only if you live in the United States. In Canada, you could be excused for not knowing such a debate exists .
Ever since FBI director James Comey characterized the rising tide of encrypted data as “going dark” in an October, 2014 speech, American civil liberties groups, cryptographers, private companies and politicians have argued ceaselessly about encryption’s merits and the dangers of so-called backdoors.
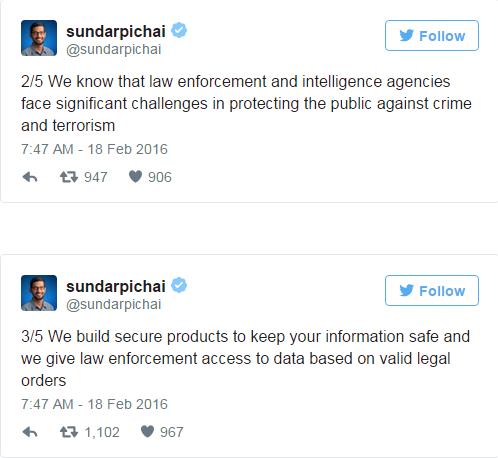
While most acknowledge that encryption keeps vast swaths of Internet communication and services secure, there have nonetheless been calls for legislation, “golden keys” and the formation of encryption committees in response to increasingly vocal arguments that encryption is helping criminals and terrorists operate beyond the law’s reach.
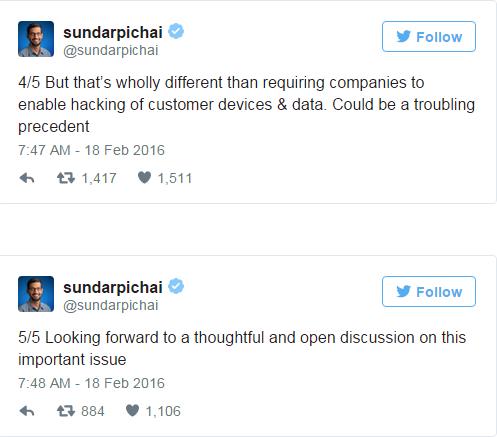
Things culminated last week with the FBI’s order that Apple Inc. modify its software to make it easier for law enforcement to break the iPhone’s security protections – modifications that have been characterized as a backdoor for law enforcement, or criminals, to use again and again.
In Canada, however, policy discussions involving encryption and, more largely, police powers in the digital realm – such as cellphone tracking devices and the use of hacking tools – have been “functionally non-existent,” according to Citizen Lab researcher Christopher Parsons.
“We haven’t had the kind of debate and back and forth and public positions taken that you see in the United States, you see in the United Kingdom. We just don’t do it here,” Mr. Parsons said.
Some of the reasons are familiar. There is, for example, a comparatively smaller policy community in Canada that focuses on these issues than there is in the U.S., and a smaller amount of case law – not to mention the fact that previous governments have shown more interest in expanding police powers, rather than curtailing or even detailing them.
And if past U.S. cases are any indication, the government will just as easily benefit by staying out of the debate and piggybacking on the outcome of the FBI’s case.
“They can dodge the debate and benefit from it without having to engage in it,” said Tamir Israel, a staff lawyer with the Canadian Internet Policy and Public Interest Clinic. “And then the other side to that is they often will find quieter ways to get comparable results where they can’t directly piggyback.”
By way of example, Mr. Israel pointed to the Solicitor General’s Enforcement Standards (SGES), which outline 23 technical surveillance standards that must be followed as a condition of obtaining a wireless spectrum licence in Canada. After the U.S. passed lawful surveillance legislation called the Communications Assistance for Law Enforcement Act in the 1990s, Canada used the SGES to quietly introduce similar standards.
Although the standards were introduced in the mid-1990s and updated again in 2008, details were not made public until The Globe and Mail obtained past and current versions of the documents in 2013.
Mr. Israel pointed to a wider problem preventing a successful encryption debate in Canada: a lack of transparency surrounding the government’s position and policies. He raised cellphone tracking technology called Stingrays, or IMSI catchers, as an example. “I personally find it very hard to believe that no law enforcement agencies in Canada are using these. But we can’t even get the debate going, because we can’t get past that first step where any of them admit that they’re using them.”
The RCMP would not comment on Apple’s dispute with the FBI but said in a statement: “International police agencies are all in agreement that some ability to access evidence when judicial authorization is granted is required, recognizing that secure data and communications enables commerce and social interactions in today’s reality. These are complex challenges which the RCMP continues to study.”
The statement continued: “The RCMP encourages public discourse with Canadians as public policy continues to take shape on the issue of encryption.”
The Office of the Privacy Commissioner of Canada said in an e-mail that it was not aware of any government agencies that have proposed backdoors in Canadian companies or Internet service providers, and that it is following encryption discussions “with interest.”
When reached via e-mail, Liberal MP Robert Oliphant, who chairs the standing committee on public safety and national security, wrote that, “while encryption and backdoors are of great concern to a number of people, they have not yet surfaced as issues for our committee in its early days.”
However, he added, the committee is still “sifting through all the important issues of safety and security and will be setting our work plan shortly.”
Public Safety Canada said in a statement that it is “monitoring the ongoing debate in the U.S. and other countries on the issue of government access to encrypted data” and that “no special events related to encryption” are currently planned.
NDP MP and committee vice-chair Brian Masse, echoing Mr. Oliphant’s statement, added that any proposed legislative changes involving encryption or backdoors should be handled democratically and involve both the Privacy Commissioner and Parliament.
Meanwhile, neither the chair nor vice-chairs of the standing committee on industry, science and technology responded to a request for comment.
A small comfort, Citizen Lab’s Mr. Parsons argued, is that Canadian politicians have shown themselves to be more level-headed and avoided the sky-is-falling rhetoric of their counterparts in the U.S., where Senator Dianne Feinstein, who chairs the Senate select committee on intelligence, stated earlier this month that “an Internet connection and an encrypted message application” is all Islamic State militants need to carry out an attack.
If this issue is going to be given some weight, Mr. Parsons suggested, “committee meetings that very seriously look into this while there isn’t a terror moment, it’s the ideal way of going.”