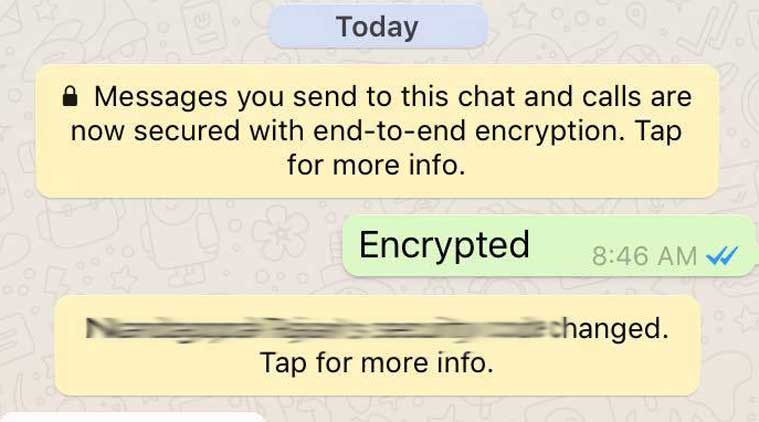
Facebook has started to introduce a setting to its “Messenger” app that provides users with end-to-end encryption, meaning messages can only be read on the device to which they were sent.
The encrypted feature is currently only available in a beta form to a small number of users for testing, but it will become available to all of its estimated 900-million users by late summer or in the fall, the social media giant said.
The feature will be called “secret conversations”.
“That means the messages are intended just for you and the other person – not anyone else, including us,” Facebook announced in a blog post.
The feature will also allow users to set a timer, causing messages to expire after the allotted amount of time passes.
Facebook is the latest to join an ongoing trend of encryption among apps.
Back in April, Whatsapp, which is owned by Facebook and has more than a billion users, strengthened encryption settings so that messages were only visible on the sending and recipient devices.
Whatsapp had been providing limited encryption services since 2014.
The company says it is now using a powerful form of encryption to protect the security of photos, videos, group chats and voice calls in addition to the text messages sent by more than a billion users around the globe.
Controversy
Encryption has become a hotly debated subject, with some US authorities warning that criminals and armed groups can use it to hide their tracks.
“WhatsApp has always prioritised making your data and communication as secure as possible,” a blog post by WhatsApp co-founders Jan Koum and Brian Acton said, announcing the change at the time.
Like Facebook has until now, Google and Yahoo use less extensive encryption to protect emails and messages while they are in transit, to prevent outsiders from eavesdropping.
Apple uses end-to-end encryption for its iMessage service, but some experts say WhatsApp’s method may be more secure because it provides a security code that senders and recipients can use to verify a message came from someone they know – and not from a hacker posing as a friend.