If you thought browsing securely (and privately) was as easy as opening a new incognito window, think again.
Private browsing is all the rage now that it’s necessary in order to access certain websites in some countries. Luckily, there are lots of ways to access the web that doesn’t require Safari, Firefox, or Chrome. There are also ways to surf the internet that aren’t actually secure at all — even if they’re advertised as such. The first step to tapping into a safe connection is understanding what a safe connection is — and what it’s not.
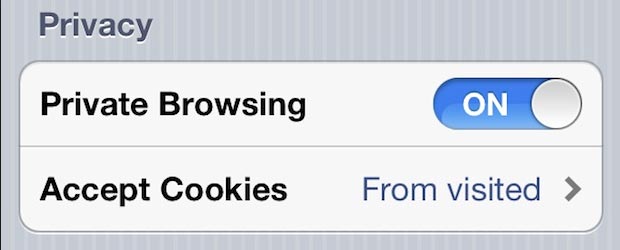
This is not what private browsing looks like.
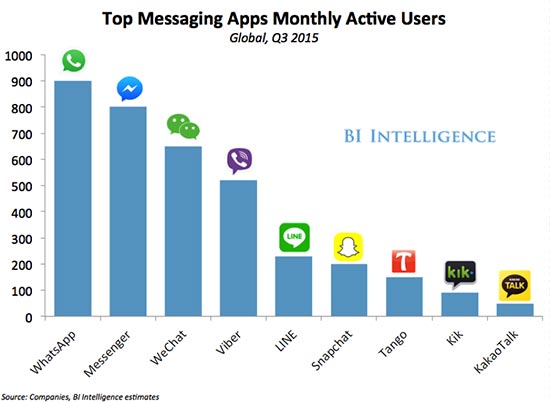
Google Chrome’s Incognito mode may cover your tracks online locally, but it doesn’t erase them entirely. When you choose to browse privately using a major web browser, the places you visit online will not accumulate in your computer’s history. This way, no one else who accesses your device will be able to see the websites you used during your private browsing session. (In fact, you won’t even be able to see them yourself.)
Except…you can. In fact, anyone can; That is, anyone who has access to your internet bill. All it takes is calling up your internet service provider and requesting a log of the websites you visited at any given time and day. (Yes, this can include times and days when you were browsing “privately.”)
Yet you and anyone with access to your internet bill aren’t the only ones with access to your browsing history! All of the websites you’re visiting can also see you, even if you’re not logged into an account associated with their services. This is because your path to that website isn’t protected. Online, who you are is defined by how you arrived there.
Encryption is the Key
Truly private browsing requires an encrypted connection through a browser that has Virtual Private Network (VPN) capabilities. This isn’t your typical browser, but rather a special kind that you may have to do a bit of Googling to find (that is, unless you’re lucky enough to find yourself reading this article).
When you connect to the internet through a VPN, where your connection originates is indistinguishable. This is because your connection is made possible through a web of devices and a remote server (some private browsers allow users to choose from a number of remote servers, but most don’t). Unlike when you connect to the web using a standard connection, when you browse through a VPN, your device’s point of origin is unidentifiable.
The only thing that is visible when you’re browsing utilizing a VPN, is the location you choose to be visible. Private browsers with VPN capabilities allow you to choose from connections around the world to display as your point of origin. (If you connect through a VPN location in Switzerland, it will appear as though you are browsing the web via Switzerland, even if your physical location is Palo Alto, California.)
Encrypted Browsing in the Work Place
In the workplace, things get a bit more complicated. Although a VPN connection will encrypt your traffic, your employer’s IT department may be able to still tell if you are using an encrypted connection especially if you’re on the company network. This may be against your company’s policy, so be aware of the consequences.
Also if you’re on a company machine, then it may already be controlled by corporate and your activities are already being monitored regardless if a VPN is on or not. The safest bet is use to a VPN on your own personal device over data and not on your company network to keep your browsing private from your employer.
How to Choose a Private Browser
There are many private browsers out there that are completely free, which is why choosing the right one to do the job can be a daunting task. Ever since the rise in popularity of private browsing in recent months, some have even adopted questionable means of serving their users (including feigning VPN capabilities and selling data).
The first thing to note when shopping for a private browser is what makes it private. If the only thing advertised is an ability to delete your local history, then you’re being pushed a glorified incognito window. Almost all today’s browser’s incognito mode does not encrypt your traffic.
The first thing that should be advertised is what VPN options the browser offers. A user friendly private encrypted browser will have different servers to connect to the web through, easy ways to switch between servers, as well as an intuitive interface for connecting, and disconnecting from the web.
Encryption is crucial for truly private browsing because it masks information about your surfing habits such as how long you stayed on a site, how many times you visited, and what your activity log looked like for any particular website. Someone snooping on your online activity may be able to see how much data you’re using in a browsing session, but they won’t be able to see how it’s used if your connection is encrypted.
There are a number of quality private browsers out there that can be downloaded for free, but it’s important to lookout for any hidden catch. When a web product or service is offered for free, sometimes the reason for that is because you’re paying for it with your data.
Other Ways to Stay Safe Online
Browsing privately isn’t the only way to protect your data on the internet. You can start using these tools even without a private browser to enhance your traditional web experience and make it harder to be tracked.
Start by switching up your default search engine. Google’s AdSense makes a private browsing experience impossible using Google. A private search engine such as DuckDuckGo and StartPage don’t creep on your habits for the sake of targeting advertisements to you.
If you browse the web primarily from your phone, be sure to turn off Geotagging to prevent the public caching of your physical location each time you take a photo. (If you’re using a private browser but still have this feature turned on, your browsing location with conflate with your physical location.)
There are many free password managers available that will help you generate passwords that are difficult to be compromised, and will remind you when it’s time to change up your passwords.
Last but not least, you can use browser security tools such as HTTPS Everywhere and Privacy Badger to protect your data even when you’re not browsing privately.