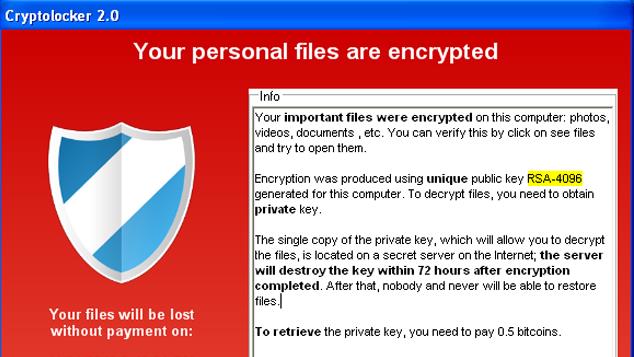
Most of the time we discuss encryption as a way to protect ourselves online , but an increasingly popular form of digital attack uses it as an extortion tool. Criminals are stealing personal files, encrypting them, and hold them hostage until their targets pay for the decryption key.
A report from security firm Symantec details a sharp rise “crypto-ransomware,” its term for this devious form of online crime, noting that these incidents were 45 times more common in 2014 than 2013, with over 340,000 people and organization unable to access files that had been encrypted by extortionists. Usually the extortionists ask their targets to pay in Bitcoin on a website accessible by Tor.
To infect computers, would-be criminals will send malicious e-mail attachments that look like bills or invoices. If you are foolish enough to open the attachment, you’re snared. It’s possible we’re seeing a rise in crypto-ransomware attacks because phishing emails where you’re tricked into opening a malware attachment or bad link are a major way that people get hacked .
There’s a growing underground economy devoted to carrying out crypto-ransomware attacks, with groups like Cryptolocker and Cryptowall selling their services. Your main line of defense is backing up all your files, since you won’t need to pay to get them back if you can just restore them. There are also services popping up to thwart crypto-ransomware, like Decryptolocker, which used a version of Cryptolocker to figure out how to decrypt files that Cryptolocker holds hostage. A service called Cryptoprevent is designed to stop this type of ransomware from a variety of different attackers.
Ransomware is still a relatively rare and aggressive cybercrime, so the likelihood of someone crypto-ransoming your vacation photos is low. No need to panic. Much more common: Phishing attacks of all kinds. A security report released by Verizon today underlines how often people fall for them. With phishing attacks, prevention is even simpler than backing up your files: Just don’t click on sketchy shit!