For modern enterprises, the trend in information computerization’s development means the data is not only the assets, but is the reflection of enterprise’s core competitiveness. To make your enterprises remain invincible in the fierce business competition, you should protect the sensitive and key data of enterprise effectively. In reality, data leakage will lead to economic losses or even more troubles.
With the development of Internet, the boundary between Intranet and Extranet is becoming blurred because the Intranet and outside world have been linked closely by Email and IMs. Traditional preventive measures like Firewall, Intrusion Detection and Anti-Virus appeared to be inadequate in the protection of sensitive data.
Why Enterprises establish Leakage-proof system
For enterprises, the internal data security is closely bound up with the enterprise security and normal operation of routine work. In some special circumstances, data security is the major part of business, directly related to the survival of enterprise. Based on this case, it is necessary to establish the relevant strategies, so that the effective leakage-proof system can be set up. Only in this way, the enterprise security can be ensured.
From the point of system value, it’s the question that data leakage in two areas, that is transmission and storage. From a security perspective, it needs a more comprehensive safety and preventive mechanism to realize the all-round protection. So how can we protect the enterprises’ data security fundamentally?
How encryption software works in enterprises’ data leakage-proof
To secure the data security of enterprise by the roots, it is suggested to choose a professional encryption software to encrypt data, because the encryption works on the data directly. As long as the encryption algorithm is not cracked, the data still remains safety.
Here an excellent encryption software called Best Encryption Expert is highly recommended, which supports features like file encryption, folder encryption, data shredding, folder protection and disk protection. Besides, there are various encryption types for users to choose. The encrypted files are copy-proof, remove-proof and delete-proof, in this way, the possibility of file leakage reduces a lot, while the security promotes greatly.
How to encrypt data with Best Encryption Expert
1. Download the software from official website or other download sites, and then install it.
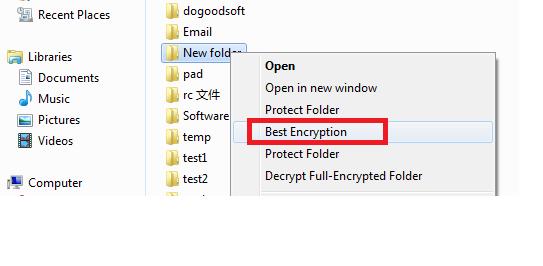
2. Right-click a file to encrypt, and then choose Best Encryption in the system menu.
3. Enter the encryption password in the pop-up window, choose the favorable encryption type, and then click “OK”, that’s it.
Official download address: http://www.dogoodsoft.com/best-encryption-expert/free-download.html