A new ransomware threat known as Bart is experimenting with the price it charges victims and encryption strategies.
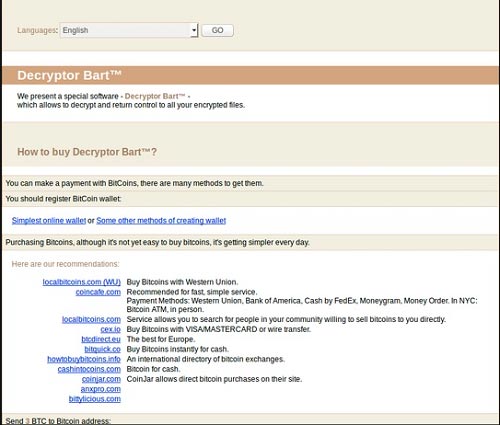
If your PC is infected by Bart you will be asked to pay three Bitcoin (BTC) or just under $2,000 to regain access to your files, which is significantly more than the usual 0.5 BTC ($300) to 1.5 BTC fee.
Also, you won’t get a decryption key, but rather a password that opens password-protected ZIP archives, where the files of Bart-infected machines have been copied.
While .zip is intended primarily for compression, it also offers encryption. However, as PC World recently pointed out, the program used to create and open the ZIP file determines whether the weak ZipCrypto encryption or the tougher-to-crack AES-256 is used.
Security firm PhishMe noted on Friday that Bart’s use of .zip files for encryption differs from most file encrypting ransomware, which traditionally use a more sophisticated asymmetric, public-private key pair for encryption.
Another distinguishing feature of Bart is that it doesn’t rely on command and control infrastructure in order to tell which PCs the malware should proceed to encrypt and provide instructions to pay the ransom.
Security firm Proofpoint also reported the emergence of Bart on Friday, and said that instead of using a command and control host, it relied on a unique browser identifier in the URL.
The Bart ransomware also won’t run if it detects the user’s system language is Russian, Ukranian, or Belorussian, according to Proofpoint.
Proofpoint also found links between the Bart ransomware and the more widely used Locky ransomware, such as a similar looking payment page, and that it like Locky it is being distributed in spam email. However, Proofpoint also found that the ransomware code itself was “largely unique” from Locky.