WhatsApp’s end-to-end encryption might still be a contentious issue, but on Wednesday the Supreme Court refused to allow a PIL seeking a ban on the popular app and similar messenger services.
The PIL, filed by Gurugram-based RTI activist Sudhir Yadav, said these apps have complete encryption, which poses a threat to the country’s security.
A bench of Chief Justice T S Thakur and Justice A M Khanwilkar rejected the PIL, suggesting Yadav could approach the government or Telecom Regulatory Authority of India (TRAI) with his plea.
But Yadav said his application to the department of telecommunication and the government got the response that they did not possess information in this regard. The petitioner contended that end-to-end 256-bit encryption introduced by WhatsApp in April made all messages, chat, call, video, images and documents end-to-end encrypted, and thus it was impossible for security agencies to decode these.
According to him, this could be national security threat for India, as agencies will not be able to track terrorists, who can plan attacks without worrying that the government can access their messages. The RTI petitioner sought to maintain a balance where police agencies can get lawful access to data while keeping information private.

So what is WhatsApp’s end-to-end encryption and why has it become such an issue? For starters, WhatsApp’s end-to-end encryption ensures that a user’s messages, videos, photos sent over the app, can’t be read by anyone else — not WhatsApp, not cyber-criminals, not law-enforcement agencies. Even calls and group chats are end-to-end encrypted.
End-to-end encryption means encryption at the device level and thus your chats, messages, videos are not stored on WhatsApp’s servers at all. The only way to access this data is if your device is compromised and the messages have not been deleted. This encryption is designed to keep out man-in-the-middle attacks.
Given WhatsApp has over a billion users, this end-to-end encryption is a big deal. Let’s not forget that in Brazil, a senior WhatsApp executive was jailed because the company did not hand over data in a court case. WhatsApp claimed the data is encrypted and it does not have access to it.
WhatsApp co-founder Jan Koum, in fact, is known for dedication to user privacy and this is also one of the reasons the app has never sold ads. When WhatsApp announced the end-to-end encryption, Koum wrote, “People deserve security. It makes it possible for us to connect with our loved ones. It gives us the confidence to speak our minds. It allows us to communicate sensitive information with colleagues, friends, and others. We’re glad to do our part in keeping people’s information out of the hands of hackers and cyber-criminals.”
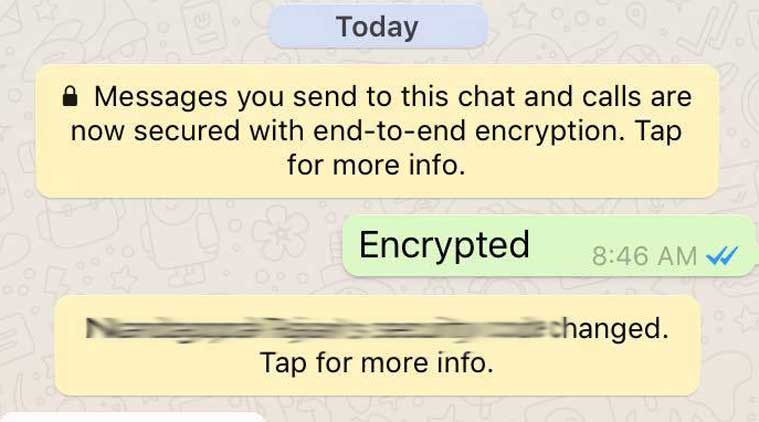
WhatsApp has relied on the “The Signal Protocol”, designed by Open Whisper Systems for its end-to-end encryption. What is also significant is the feature is enabled by default on WhatsApp, unlike apps like Telegram where you have to go into a secret chat mode for end-to-end encrypted chats.
WhatsApp is also one of the most popular apps in India. In fact, research has consistently shown it is one of most used apps after Facebook, and it is common for most people in India to be part of various groups on the service. Family, School, College friends, even office groups are present on WhatsApp. End-to-end encryption means all of this data is secure, and can’t be accessed by third-parties including government agencies.
For now the Courts have refused to go for a ban on WhatsApp, and instead directed Yadav towards the government. India per se doesn’t have a law on what kind of encryption third-party apps can used.
As we had noted earlier, the 40-bit encryption limit, which is too low given the current times, is something ISPs and TSPs have to stick with and doesn’t apply to apps.
Until India comes up with an encryption law, WhatsApp remains legal and we’ll have to wait and watch how the encryption versus security agency debate plays out in the country.