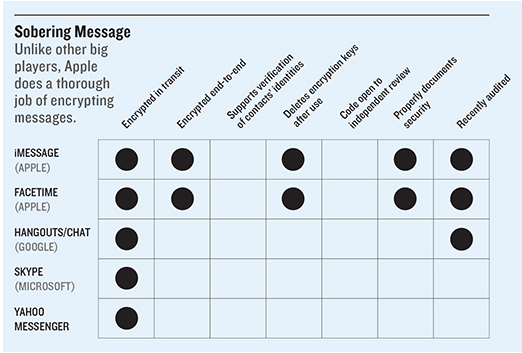
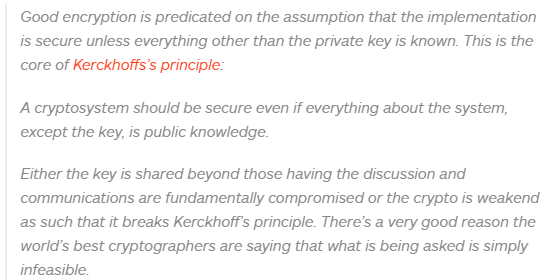
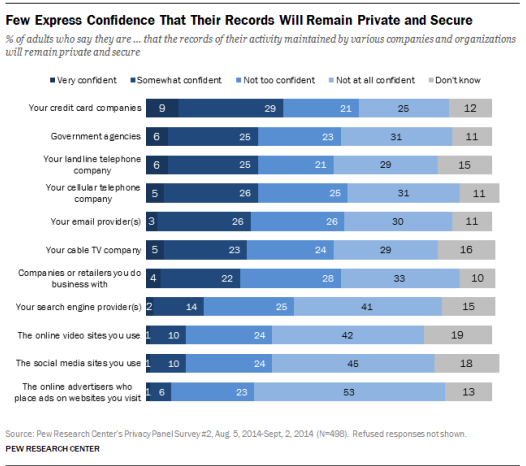
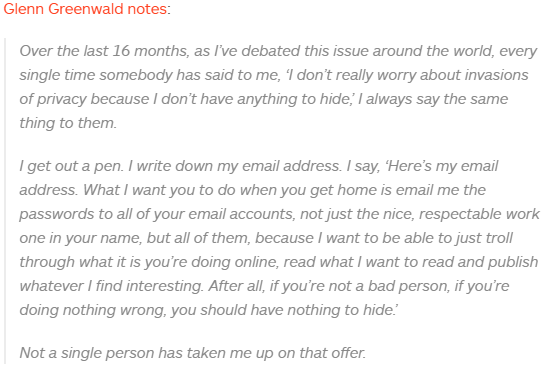
A consumer alert issued by Victoria’s Legal Services Commissioner a few weeks ago raised, to our mind, an old and curious issue. Why aren’t Australian professionals required to secure their email?
Eighteen years ago, Victoria’s Law Institute Journal carried an excellent feature article on the ease with which email can be forged, the fact that it was already happening and the gold standard technology for mitigating the risk, digital signatures and encryption. We have to say it was excellent, since we wrote it, but it did get a lot of attention. It even won an award. But it had no practical impact at all.
Fast forward to 2016 and the same State’s Legal Services Commissioner is alarmed by a UK report of an email hoax that fleeced a newly married couple of their home deposit. Just when they were waiting for instructions from their lawyers on where to transfer their hard earned ₤45,000, fraudsters sent a bogus message that impersonated the attorneys and nominated a false bank account. The hapless couple complied and the scammers collected their cash.
UNSECURED SYSTEM
The Victorian Commissioner’s alert includes several good points of advice to consumers, like being cautious about links and attachments in emails from unfamiliar senders and using antivirus software. But curiously, it doesn’t canvass the key technology question raised in the UK report: Why wasn’t the lawyers’ email secured against forgery?
The newlywed groom pointed the finger right at the problem, quoted as saying “‘Losing this money is bad enough. But what makes it worse is that this could have all been avoided if our emails had been encrypted. It seems crazy to ask us to transfer such huge amounts by sending a bank account number.”
The lawyers’ response: “Advantage Property Lawyers said that the firm was not responsible for the couple’s loss. It said its emails were not encrypted but that this was standard industry practice. We stick to the highest industry standards in all aspects of our business.”
So non-encryption, fairly described by Joe Public as crazy, is the standard industry practice in the UK, just as it is in Australia.
There may be more to this than meets the eye. A couple of years after our 1997 article, we were asked to host a media lunch for Phil Zimmerman, the US tech wizard who created the first user friendly email encryption and signing software. We invited a senior officer of the Law Institute, thinking the topic would be of vital interest. Apparently not.
Over lunch, Zimmerman offered to supply the Institute with free copies of the tool so it could lead the profession down the road of best practice. For reasons we didn’t understand then and still don’t, the offer created no interest.
LACK OF INTEREST
We recounted the story of that lunch in this column years later, wondering if that would spark some enquiry into the options for fighting exactly the kind of fraud that’s happening in the UK. Silence. It seems that, at the highest levels, legal eagles’ eyes glaze over when the topic of secure email arises. As long as the entire profession ignores the issue, we can all say that “our emails are not encrypted but this is standard industry practice.”
For the record, encryption can help secure email in two ways. First, it can prove that a message is from an authenticated sender, and hasn’t been tampered with in transit. Optionally, it can also scramble the contents of messages so only the intended recipient can read them. Implementing these protections requires some centralised infrastructure and a way to ensure it is used by the target audience. Australia’s law societies are ideally placed to sponsor a more secure system, especially now that a uniform national legal practice regime is in operation.
We used Zimmerman’s product for a couple of years, and it was simple. Using an Outlook plug in, you clicked a button to send a signed message. You entered a password, the software worked its magic in the background, and a digital signature was applied. We gave it up when it became clear that insecure email was set to remain industry best practice for years to come.
Back in 1997, we wrapped up our article with the wildly inaccurate prediction that “in two years, all commercial documentation will be digitally signed. Lawyers have every reason to lead the way.”
Here’s hoping it doesn’t take another 18 years.