As Apple resists the US government in a high profile stand-off over privacy, rival device makers are, for now, keeping a low profile.
Most are Asian companies — the region produces eight of every 10 smartphones sold around the world — and operate in a complex legal, political and security landscape.
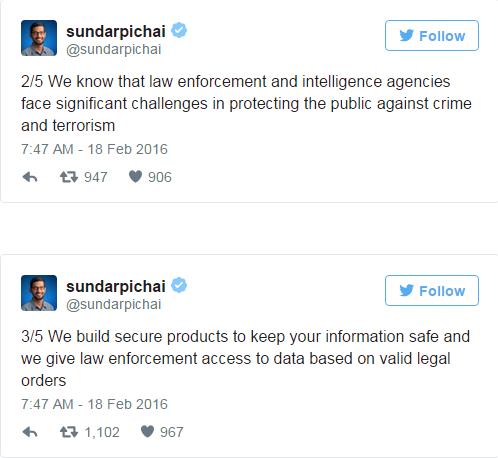
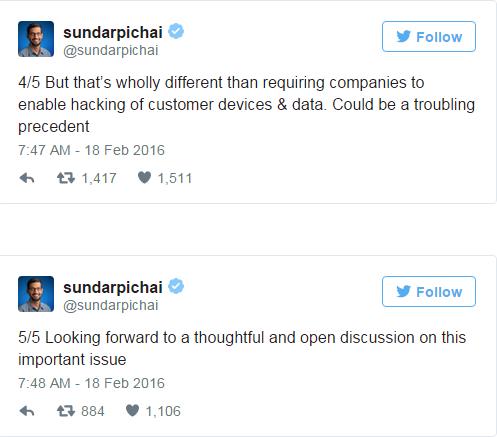
Only China’s Huawei has publicly backed Apple CEO Tim Cook in his fight to resist demands to unlock an encrypted iPhone belonging to one of those who went on a shooting rampage in San Bernardino, California in December.
“We put a lot of investment into privacy, and security protection is key. It is very important for the consumer,” Richard Yu, chief executive of Huawei’s consumer business group, told reporters at the Mobile World Congress earlier this week.
But Yu stopped short of saying explicitly that Huawei would adopt the same stance. “Some things the government requires from vendors we cannot do,” he said, citing an example of unlocking an encrypted Android device. “These are important things for the consumer, for privacy protection.”
Lenovo Group CEO Yang Yuanqing declined to say whether he backs the Apple position, saying the issue required time and consideration.
“Today it happens to Apple, tomorrow it could happen to Lenovo mobile phones. So we must be very serious to consider. We need to take some time,” Yang told Reuters.
Samsung Electronics Co and Chinese device maker Xiaomi declined to comment, while ZTE Corporation did not respond to requests for comments.
South Korean mobile maker LG Electronics Inc said it takes personal privacy and security very seriously, but declined to say whether it had ever worked with any government to insert so-called “backdoors” into its products or whether it had ever been asked to unlock a smartphone.
“Nobody wants to be seen as a roadblock to an investigation,” said a spokesperson for Micromax, India’s biggest local smartphone maker. “Nobody wants that kind of stigma. We have to take care of both customer security as well as (a) genuine threat to national security.”
Many Asian countries don’t have privacy laws that device makers can fall back on to resist demands from law enforcement authorities.
“As part of the evidence gathering process provided for under the law, law enforcement agencies in Singapore may request information from persons or organizations,” Singapore’s Ministry of Home Affairs Spokesperson told Reuters.
An official at India’s telecom regulator said authorities can ask for private user data from technology companies, as can those in Indonesia, said Ismail Cawidu, spokesman for Indonesia’s Communication and Information Ministry.
Eugene Tan, associate professor of law at the Singapore Management University, said he wouldn’t be surprised if technology firms weren’t being asked for access to their devices.
“It’s just that these are not made public. You can imagine for the technology companies, they are also concerned about the publicity — if they are seen to be caving in to law enforcement agencies, there is always a fear that people may not use their products and services,” he said.
Micromax said this was commonplace in India. “I can’t say no to a law enforcement request, and every day there is one,” the company’s spokesperson said. “You have to comply with requests in the larger interest of national security.”
The Apple battle may even spur regulators in some markets to demand device makers to grant them access.
Thailand’s telecoms regulator said it is studying the possibility of having separate agreements with handset makers and social media firms such as Facebook and Naver’s LINE to help extract data from mobile phones.
“There is political pressure” for regulating devices, said Rob Bratby, manager of Olswang Asia, a technology-focused law firm based in Singapore.
He said there was no evidence of any such regulatory interest yet, but it was a matter of time.