PC Monitor Expert is designed to record all the computer activities, which works as a good helper for parents and computer administrators. For some bugs in the version 1.62 that brought the inconvenience to software users, we have upgraded PC Monitor Expert to version 1.63.
Update information of PC Monitor Expert:
File Name: PC Monitor Expert
Version: V1.63
File Size: 3.72MB
Category: Computer monitoring software
Language: Chinese
License: Trial version
Running on: Win XP/ Vista/7/8
Released on: Apr. 23, 2015
Download from: http://www.jiamisoft.com/pcsc/download.html
What’s new in this version:
+ added screenshot support for the ransparent windows;
* refined the email sending data of monitoring information, improved email sent rate;
– fixed a bug in Email Settings;
* improved the generation of computer machine code.
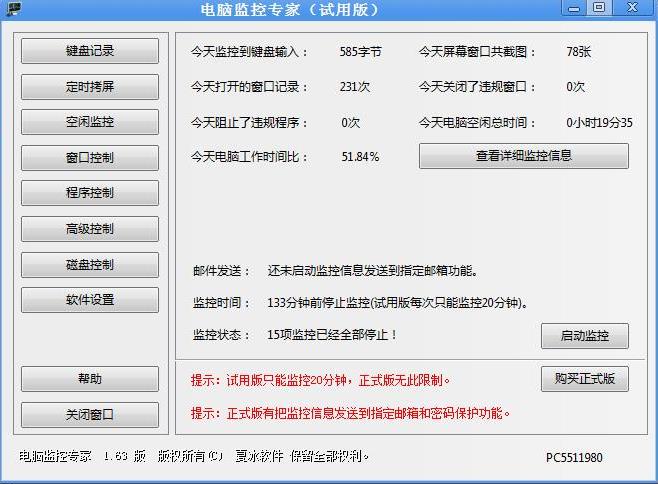
Main features of PC Monitor Expert:
1)Stealth operation: PC Monitor Expert cannot be found on the monitored computer. The monitoring software becomes invisible without any trace after installation, and it can monitor the object monitored computer secretly without letting anyone know. You can launch it by pressing hot key “Ctrl + Alt + U”.
2)Keystrokes Input Records: PC Monitor Expert can monitor all typed keystrokes, including Chinese, English, figures and functional keys. MSN or QQ chats, IMs, e-mail sent, usernames and passwords logged on some websites or e-mail can also be recorded(Warning: please DO NOT use this monitoring software for illegal use. This software won’t record sensitive passwords like QQ or MSN password).
3)Computer Screenshots Capture: Take screenshot of QQ or MSN chats window, active window or the entire compter screen. The monitored screenshots can be played automatically when you view them.
4)Opened Windows Monitoring and Control: Record all titles of opened window and the time they were opened. Prohibit opening windows containing specific block keywords in the title. For example, if you want to keep your children away from some adults contents, you can add adult contents as keyword to the prohibited list. In this way, all windows containing adults contents will be filtered automatically and PC Monitor Expert will forcibly close such web pages. Besides, this software can also record the action you open a prohibited window and opening time.
5)Running Programs Monitoring and Control: Prohibit software you specified (PC Monitor Expert has pre-configured over 30 game software). If a prohibited program is detected, PC Monitor Expert will forcibly shut it down and record this breach;
Prohibit chat software like MSN, QQ or Skype;
Prohibit using web browsers to view web pages;
Prohibit using download software to download;
Prohibit modifying system time;
Prohibit Task Manager(to prevent from ceasing active programs illegally), Registry or Control Panel etc.
6)Enhanced Functions: PC Monitor Expert can sent all monitored record (keystrokes, screenshot captured, active windows, and breaching behaviors and etc.) to a specific E-mail. You can conduct network monitoring as you wish. You can also set a password for this software and thus no one can modify settings or delete this software without the valid password. This software offers timed shutdown function with which you can schedule to shut down your computer at a certain time.
In addition, PC Monitor Expert supports disk control, which can better protect your important content.